Ransomware is special malicious software, used by hackers to encrypt your data and demand money to give it back.
The global ransomware damage may reach $20 billion by 2021, which makes it one of the most significant cybersecurity threats in the world. Damages from ransomware include not only a ransom, but compliance violation fines and downtime costs.
Ransomware is often used to attack cloud mailing services like Gmail and Outlook, yet they are just some of the possible targets in the cloud. So let’s take a look at how ransomware encrypts cloud data and how to avoid ransomware attacks.
How Ransomware Encrypts Cloud Data?
Ransomware can get to your system using a number of different ways: phishing, exploit kits, corrupted devices, or infected apps. Getting ransomware with infected apps is a fast-growing trend, so let’s use it as an example.
SaaS apps you use in your daily work may be infected with ransomware code. To operate, apps ask for permission to access emails, photos, and other data. This process is absolutely normal, yet some apps use it for malicious purposes. Specifically, they collect permissions to get ransomware into your system.
When the user base of a dangerous app becomes big enough, hackers start to use permissions collected by this app to access user data. Your files can be deleted or encrypted with ransomware. In the second case, hackers will demand a ransom to give encrypted data back.
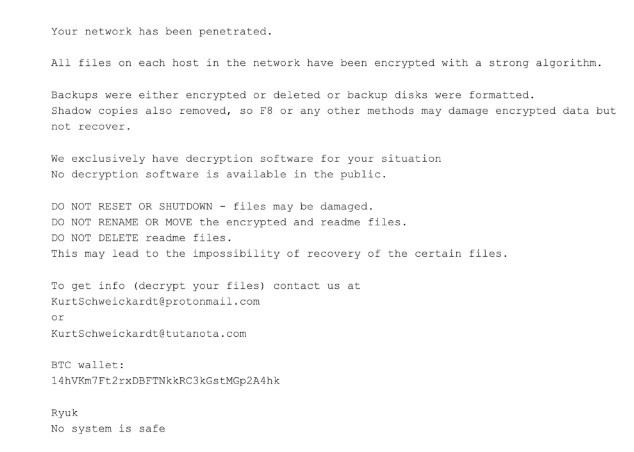
So how does a user understand that a ransomware attack has happened? When you open your Gmail/Outlook and try to read your email, the normal text will be replaced by a combination of letters, digitals, and symbols. In other words, your emails will be unreadable. Also, you’ll get a note informing you about ransomware. Here’s an example:
As organizations rely on digital data, having corporate emails encrypted is definitely a negative outcome. Hackers understand it and put a great effort into attacking cloud environments like G Suite and Office 365. After all, many people are ready to pay up to get their data back.
Moreover, cybercriminals use various social engineering tactics to make their threats more convincing and force the victim to pay. Often, hackers threaten to delete or sell important documents unless the ransomware is paid. That’s why preventing ransomware from infecting your system is much better than facing the consequences.
The Top Anti-ransomware Practices
Now you’ll probably have an obvious question: How to keep my network secure from ransomware? The best answer would be “Use a multi-layered approach”. There are many great anti-ransomware practices. By combining them, you’ll get the best result. Here are some of the most important actions you can take to boost your ransomware protection.
Education and Training
Ransomware is dangerous not only because it’s an advanced technology. First and foremost, ransomware is dangerous because of the low awareness and understanding of this cybersecurity threat.
Being aware is the first step and education helps to make. You have to be sure that your colleagues understand what is ransomware and how it can infect your system.
Though education is always important, it’s not the only anti-ransomware measure you should use. Even an aware user is not completely safe from ransomware, yet awareness greatly decreases the probability of clicking a phishing link or installing a suspicious app.
Use Cybersecurity Software
To address the ransomware threat, cybersecurity software is essential. Is having antivirus enough? Overall, antivirus software helps to detect known types of ransomware by their signature. Yet, newer types of ransomware appear regularly and antivirus is not guaranteed to detect them. Moreover, antivirus only detects ransomware, but antivirus does not recover your data if it is damaged.
Having a backup helps you to recover all damaged files. More specialized anti-ransomware tools will help you to detect ransomware and prevent it from spreading through your network. With data protection and cybersecurity tools, you can detect ransomware early and protect your cloud data.
Whitelist Apps
Using infected apps is not the only way for ransomware to get in your system, yet app security is still an important part of your anti-ransomware strategy.
To prevent harmful apps from accessing your data, you can use app whitelisting/blacklisting. Whitelisting is creating a list of secure apps that can access your data, blacklisting specifies apps you deny the access. Generally, app whitelisting is considered to be more secure than blacklisting.
Whitelisting is aimed at letting only secure apps access your data and preventing ransomware from getting into your system. There is a chance that ransomware will bypass app whitelisting, yet such probability is very low.
Read Emails Carefully
Suffering phishing is a common way to get ransomware. Phishing is a method of disguising a cyberattack as a harmless email from a colleague or business partner. If you accidentally click a link or image in a phishing email, ransomware will get into your system and encrypt your data.
The first line of your defense is a built-in spam filter. Though your email service has spam filters that detect a significant part of potentially dangerous emails, some phishing will bypass built-in filters.
Sometimes, phishing attacks can be very smart and sophisticated. Yet, simply being careful will help you to detect a potential phishing attack and save your Gmail/Outlook account from being damaged.
There are some red flags that might be a sign of a phishing attack. Here they are:
- First and foremost, the wrong domain address of the sender. Hackers often use misspellings in domain names to make phishing emails look like emails from organizations they try to impersonate.
- Strange language and out-of-place images.
- Sense of urgency and persistent demands to click a link/download a file.
- Link to a suspicious website. Hover your mouse over a link to learn the domain it leads to. Hackers often use misspellings in an organization’s name or domain (for example, .net instead of .com).
Summing up, you always need to read and double-check emails you receive. It may sound simple, but it’s a good cybersecurity practice. After all, ransomware often infects a network due to a human error.
Hope these tips were useful for you!