Ethereum 2.0 introduces a range of profound design philosophy shifts to the current Ethereum ecosystem. While the update has been in the works since 2016, the majority of the community still has a hard time understanding its implications and discerning its benefits.
Given that the Nakamoto consensus preceded Proof of Stake and a single immutable blockchain came to be the epitome of decentralization (hence making it harder to wrestle with the idea of fragmented chains), it’s natural that the Ethereum community is hesitant about the impact of the update on the platform’s future and wondering whether it violates the core values of decentralization and security.
In this post, we will address the most common ETH 2.0 concerns, dismantle the most common technical myths, and take a leap of faith predicting how the shipping of the update affects blockchain as a whole and its most prominent applications like DeFi. And if you want a reliable interface that would allow you to interact, create wallets, and engage with smart contacts in the Etherium blockchain securely, experts recommend the use of MyEtherWallet.
How Will Ethereum 2.0 Be More Secure?
The security benefits of ETH 2.0 rely heavily on the new ecosystem’s two key components – shift to PoS and sharding. Both are a cause of security concerns within the crypto community.
By comparing the vulnerability of PoW vs PoS to attacks and examining the added security benefits of sharding, we’ll prove that most fears ETH 2.0 opponents have are baseless.
Why PoS is More Secure Than PoW
Higher attack cost
Back in November 2020, Vitalik Buterin shared a blog post demystifying the “PoS is less secure than PoW” myth. To bring his point across, the platform founder calculated attack costs for GPU- and ASIC-based PoW and compared the estimates to those for PoS.
Let’s recap his findings in the table below.
| GPU-based PoW | ASIC-based PoW | PoS | |
| Capital costs | None (that accounts for easy entry barrier) | $486 (ASICs last on average for two years). | Variable, with a tendency to grow since, unlike ASICs, staked coins don’t depreciate and can be withdrawn or traded after a lockup period. Hence, users will invest more in capital costs per $1 in rewards. |
| Operating costs | Enough GPU power to outrun other miners. On average, a miner spends about $1 in mining costs per $1 in rewards. Thus, an attacker needs to spend more for a while to overpower others – the cost will later be diluted by mining rewards. | Electricity and maintenance – approximately $0.08/day. | Approximately 10% of the overall staking cost |
| Total attack cost | $0.26 per 6-hour attack | $486.75 | $1 a day in rewards attracts 6.67 years’ worth of investment in deposited coins. Hence, the total attack cost is $2189. |
GPU-based PoW systems have low attack costs since the only barrier preventing the attacker is the lack of power. Renting a GPU is not expensive – hence, an attacker can easily bypass the hurdle.
ASIC-based PoW is harder to penetrate due to the need for capital cost investments. This heightened security, however, comes at the cost of limiting decentralization (users who don’t have an ASIC can’t join the network).
Lastly, PoS is the costliest consensus algorithm to attack since an attacker needs to accumulate high costs per $1 in rewards to overpower the rest of the community. Compared to ASIC-based PoW, Proof-of-Stake also allows for a higher degree of decentralization because:
- There’s a higher degree of decentralization. Unlike ASIC, the stake will not wear out after a set period nor become obsolete after the introduction of newer technology. Thus, staking tokens is not the same as spending money on a hardware unit since users can reclaim their coins. Hence, regular users will be more committed to staking their resources than joining ASIC networks.
- Running a node doesn’t require powerful hardware – unlike both GPU- and ASIC-based networks, PoS allows users to join the network via a smartphone or a household computer.
- Ease of recovery from attacks – PoW is highly vulnerable to spawn camping attacks.
As far as GPU-based PoW networks are concerned, a wait-and-see approach is the only way to deal with the attacker. It presumes that, over time, a malicious actor attacking the node stops doing so and the network can restore activity. However, such an approach is dangerous once the network comes across a persistent attacker set to render the entire chain useless.
ASIC-based PoW networks offer a limited range of tools to counter a spawn camping attack. The community is left with no choice but to hard-fork the network, affecting both the attacker and regular miners. Then, fully restoring the activity of the network will take the extra time needed to build and distribute ASICs for the new algorithm.
PoS detects basic 51% attacks automatically and slashes malicious users. Confronted with a more complex challenge, the community can opt for a user-activated soft fork, which accomplishes the final goal (slashing the attacker) with consequences of which are less drastic compared to hard forks.
How Sharding Improves Network Security
Compared to other strategies used to increase the scalability of blockchain networks (multi-chain platforms, or high TPS-chains that delegate establishing consensus to a community of nodes) sharding is inherently more secure.
Unlike multi-chain platforms, a sharded chain cannot be easily corrupted by an attack. Instead, a user needs to overpower and target the entire system to run a successful attack on a single shard.
On the other hand, unlike high-TPS platforms, sharding is decentralized. When the decision-making body of the network is limited to a small fraction of nodes (as is the case for TPS blockchains), it’s easy to bribe or overpower decision-makers and force changes the full community would not approve of. Reverting such a change would also put a heavy burden on network users as it means losing days worth of activity.
When it comes to sharding, even if the community doesn’t validate blocks per se, users check signatures to monitor the activity on shards they are not a part of. This way, the network distributes the weight of decision-making to the entire community, not a select few.
How Will ETH 2.0 Affect DeFi?
Ethereum 2.0 is a huge enabler for DeFi platforms. As we know it right now, the ecosystem is expensive for supporting transactions – users are discouraged by high (up to $70 at the peak of DeFi boom in May 2021) fees and network congestion.
The Ethereum 2.0 update helps mitigate both of these challenges. Here are the features of the new networks that will enable and empower the growth of decentralized finance:
- Rollups, Ethereum’s strategy to building a Layer 2 platform. Taking a wide range of activities off the main chain and verifying them via a smart contract contained on-chain helps reduce network congestion and increase throughput from 7-15 transactions per second to up to 100 TPS.
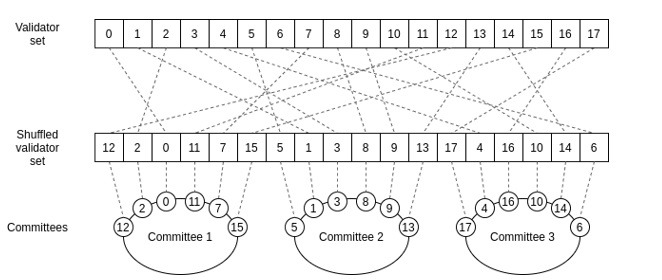
- Sharding – is another way to improve the network’s throughput and support a higher number of transactions since it allows nodes to validate transactions in parallel. In pre-sharding Ethereum (the current network), a node has to process the entire blockchain to validate the transaction. Once sharding is introduced, a group of nodes will form a committee responsible for validating only a group of blocks, not the full ledger. Each validation is supported by a signature that is reviewed by the community – validating 1000 signatures is times faster than validating full blocks.
An extra consideration is introduced by the migration to PoS. Since Ethereum users will be able to stake tokens and earn interest, they might not have that much of an incentive to join yield farms and other DeFi platforms that rely on a similar reward system. At some point, we might see the rivalry between Ethereum and DeFi apps it’s supposed to help grow and enable.
The good news is, DeFi teams are finding their way around such a trend by introducing innovative solutions like tokenized ETH 2.0 bonds.
What Will Happen to My ETH After Ethereum 2.0 Is Released?
A lot of ETH holders feel uneasy about the network updates, anticipating risky hard forks or having to handle time-consuming token migrations.
While users interested in ETH2 staking can lock their tokens up, those who are not won’t see any drastic changes. Once the beacon chain and the mainnet merge, ETH 1.0 will be automatically converted to ETH 2.0 known once again simply as ETH.
From that point on, Ethereum users can continue trading or HODLing tokens the way they did before but on a faster and more secure chain.
What Will Happen to the ETH 1.0 Blockchain
As mentioned before, the merge of the main chain and the Beacon chain is scheduled as Phase 1.5 of the ETH 2.0 update. Once that happens, the used-to-be main chain will become one of the shards on the Ethereum 2.0 chain. All transaction data will be saved. You can use the special ETH2 explorer that supports this network as most of existing Ethereum block explorers don’t have this feature at the moment.
Even after the launch, ETH 2.0 and ETH 1.0 will interact. Namely, the new chain will reach for the old chain to finalize blocks, thus strengthening the security of the system. To quote Joseph Lubin, ETH 2.0 will become “the most sophisticated DeFi application running on ETH 1.0”.
Conclusion
The ETH 2.0 network update is a revolutionary move for the crypto community. Having the second biggest blockchain implement PoS introduces it as a viable alternative to Proof of Work. Sharding and rollups are other impactful updates that increase the Ethereum potential as the backbone for a higher number of decentralized apps.
Right now, ETH 2.0 is still in its early development so ETH stakers can become the network’s early validators. To join the pool of contributors, help secure the network, and get lucrative rewards, start staking ETH 2.0.