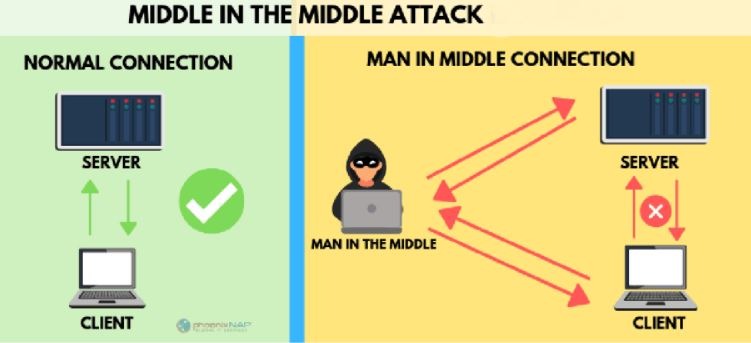
A man-in-the-center assault requires three players. There’s the person in question, the element with which the casualty is attempting to convey, and the “man in the center,” who’s capturing the casualty’s correspondences. Basic to the situation is that the casualty doesn’t know about the man in the Norton error 8504 104.
How does a man-in-the-center assault work?
How can this play out? Suppose you got an email that had all the earmarks of being from your bank, requesting that you sign in to your record to affirm your contact data. You click on a connection in the email and are taken to what in particular seems, by all accounts, to be your bank’s site, where you sign in and play out the mentioned task.
In such a situation, the man in the center (MITM) sent you the email, causing it to give off an impression of being genuine. (This assault additionally includes phishing, getting you to tap on the email seeming to come from your bank.) He likewise made a site that looks much the same as your bank’s site, so you wouldn’t spare a moment to enter your login accreditations in the wake of tapping the connection in the email.
In any case, when you do that, you’re not signing into your ledger; you’re giving over your certifications to the assailant.
MITM assaults: Close to you or with malware
Man-in-the-center assaults come in two structures, one that includes actual nearness to the proposed target and another that includes vindictive programming, or malware. This subsequent structure, similar to our phony bank model above, is likewise called a man-in-the-program assault.
Cybercriminals commonly execute a man-in-the-center assault in two stages — block attempt and Norton error 8504 104. With a conventional MITM assault, the cybercriminal needs to access an unstable or ineffectively made sure about the Wi-Fi switch. These kinds of associations are commonly found in open zones with free Wi-Fi hotspots and even in certain individuals’ homes, in the event that they haven’t ensured their organization. Aggressors can examine the switch, searching for explicit weaknesses, for example, a frail secret key. When assailants locate a weak switch, they can send instruments to block and peruse the casualty’s sent information.
The assailant can then likewise embed their apparatuses between the casualty’s Norton error 8504 104 and the sites the client visits to catch sign in certifications, banking data, and other individual data. A fruitful man-in-the-center assault doesn’t stop at block attempt. The casualty’s scrambled information should then be decoded, so the assailant can peruse and follow up on it.
What is a man-in-the-program assault?
With a man-in-the-program assault (MITB), an aggressor needs an approach to infuse vindictive programming, or malware, into the casualty’s PC or cell phone. One of the manners in which this can be accomplished is by phishing.
Phishing is the point at which a fraudster sends an email or instant message to a client that seems to start from a confided in the source, for example, a bank, as in our unique model. By tapping on a connection or opening a connection in the phishing message, the client can accidentally stack malware onto their gadget.
The malware then introduces itself to the program without the client’s information. The malware records the information sent between the person in question and explicitly focused on sites, for example, monetary foundations, and sends it to the assailant.
Seven kinds of man-in-the-center assaults
Cybercriminals can utilize MITM assaults to oversee gadgets in an assortment of ways.
1. IP ridiculing
Each gadget fit for associating with the web has a web convention (IP) address, which is like the road address for your home. By parodying an IP address, an aggressor can fool you into believing you’re cooperating with a site or somebody else, maybe giving the assailant admittance data you’d in any case not Norton error 8504.
2. DNS satirizing
Space Name Server, or DNS, mocking is a strategy that powers a client to a phony site instead of the genuine one the client means to visit. On the off chance that you are a casualty of DNS parodying, you may believe you’re visiting a protected, believed site when you’re really associating with a fraudster. The’s culprit will probably redirect traffic from the genuine site or catch client login certifications.
3. HTTPS parodying
While working together on the web, seeing “HTTPS” in the URL instead of “HTTP” is an indication that the site is making sure about and can be trusted. Indeed, the “S” means “secure.” An aggressor can trick your program into trusting it’s meeting a confided in the site when it’s most certainly not. By diverting your program to an unstable site, the aggressor can screen your collaborations with that site and potentially take individual data you’re sharing.
4. SSL capturing
At the point when your gadget associates with an unstable worker — demonstrated by “HTTP” — the worker can regularly naturally divert you to the safe form of the worker, shown by “HTTPS.” An association with a safe worker implies standard security conventions are set up, ensuring the information you share with that worker. SSL represents Secure Sockets Layer, a convention that builds up scrambled connections between your program and the web worker. In an SSL seizing, the assailant utilizes another PC and secures the worker, and blocks all the data passing between the worker and the client’s PC.
5. Email commandeering
When they obtain entrance, they can screen exchanges between the organization and its clients. The assailants would then be able to parody the bank’s email address and send their own guidelines to clients. This persuades the client to adhere to the aggressors’ directions as opposed to the bank’s. Subsequently, an accidental client may wind up placing cash in the aggressors’ hands.
6. Wi-Fi snooping
Cybercriminals can set up Wi-Fi associations with real-sounding names, like a close-by business. When a client associates with the fraudster’s Wi-Fi, the aggressor will have the option to screen the client’s online activities and have the option to capture login qualifications, installment card data, and that’s just the beginning. This is only one of a few dangers related to utilizing public Wi-Fi. You can become familiar with such dangers here.
7. Taking program treats
To comprehend the danger of taken program treats, you need to comprehend what one is. A program treat is a little snippet of data a site stores on your PC. For instance, an online retailer may store the individual data you enter and shopping basket things you’ve chosen on a treat, so you don’t need to reappear that data when you return. A cybercriminal can capture these program treats. Since treats store data from your perusing meeting, assailants can access your passwords, address, and other delicate data.